Hackers gain access to Canon Business Process’s personal data using a phishing scam
Exploit: Phishing scam
Canon Business Process: Business outsourcing provider
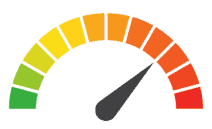
Risk to Small Business: 1.575 = Severe: After an employee fell for a phishing scam, hackers gained access to the personal data from the company’s business contracts, including General Electric. The breach occurred between February 3 and February 14, 2020, but Canon Business Process didn’t learn of the breach until February 28. Now, in addition to providing credit monitoring services for victims, Canon Business Process has damaged its reputation with a major client.

Individual Risk: 1.701 = Severe: Canon Business Process provides outsourcing services for human resources and payroll responsibilities, so the compromised data includes direct deposit forms, tax forms, Social Security numbers, birth certificates, passports, benefit applications, and driver’s licenses. This information is often used to execute financial fraud, and those impacted by the breach should immediately notify their financial institutions of the breach. In addition, they should enroll in the complimentary credit monitoring services provided by Canon Business Process.
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Third-party data breaches are becoming increasingly common, extending businesses’ cybersecurity concerns to every partnership they pursue. With the cost and consequences of a data breach continually increasing, every company should consider a company’s defensive posture before agreeing to work together.
Risk Levels:
1 - 1.5 = Extreme Risk
1.51 - 2.49 = Severe Risk
2.5 - 3 = Moderate Risk
*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.

