Oregan DHS Breach Exposes Personal Information of 645,000 Citizens
Exploit: Phishing attack
Oregon Department of Human Services: State government agency supporting safety and health initiatives
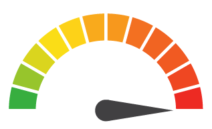
Risk to Small Business: 1.444 = Extreme: When nine employees clicked on a phishing email, hackers gained access to their accounts, which collectively included more than two million emails containing personal information. The data breach occurred in January 2019, and it was first reported in March. However, the agency’s forensics investigation identified nearly twice as many impacted accounts as initially disclosed. Although phishing scams are entirely defensible, relying primarily on apathy and ignorance to trick unsuspecting recipients, the Oregon Department of Human Services is now responsible for providing 12 months of identity monitoring and recovery services as well as a $1 million insurance reimbursement policy to those who were impacted by the breach.
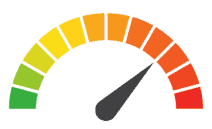
Individual Risk: 2 = Severe: When hackers gained access to the employees’ email accounts, they received an incredible amount of personal information. This data could include names, addresses, birth dates, social security numbers, case numbers, personal health information, and other sensitive information. Oregon DHS is offering identity monitoring and recovery services to those impacted by the breach
Customers Impacted: 645,000
How it Could Affect Your Customers’ Business: Phishing attacks are on the rise, delivering malware that can cripple a company’s reputation and financial standing. Fortunately, they are also entirely defensible. With proper training, employees can be transformed into the strongest line of cybersecurity defense, rather than an imminent liability. Given the high cost of a data breach, the relatively minor expense of a training program is an obvious solution for any organization.
Risk Levels:
1 - 1.5 = Extreme Risk
1.51 - 2.49 = Severe Risk
2.5 - 3 = Moderate Risk
*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.