Exploit: Phishing
University of San Diego Health: Hospital System
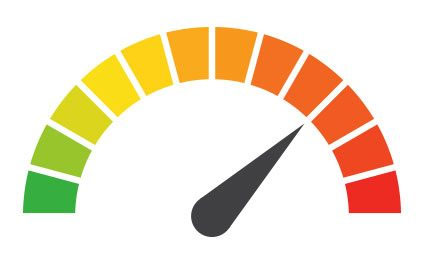
Risk to Business: 1.663 = Severe
UC San Diego Health has disclosed a data breach after the compromise of some employees’ email accounts. UC San Diego Health discovered that cybercriminals had gained access to some of its employees’ email accounts through a phishing attack. The attackers may have accessed the personal information of patients, employees and students between December 2, 2020, and April 8, 2021.

Risk to Individual: 1.271 = Severe
Potentially impacted information includes: patients’ full name, address, date of birth, email, fax number, claims information (date and cost of health care services and claims identifiers), laboratory results, medical diagnosis and conditions, Medical Record Number and other medical identifiers, prescription information, treatment information, medical information, Social Security number, government identification number, payment card number or financial account number and security code, student ID number and username and password. The hospital will offer free credit monitoring and identity theft protection services through Experian IdentityWorks for one year and is contacting impacted individuals via mail.
Customers Impacted: 55,000
How it Could Affect Your Customers’ Business Medical data is some of the hottest data to sell in dark web markets, earning cybercriminals a substantial profit and this hospital substantial fines under HIPAA and California Privacy regulations.
Risk Levels:
1 - 1.5 = Extreme Risk
1.51 - 2.49 = Severe Risk
2.5 - 3 = Moderate Risk
*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.

