Children’s Choice Pediatrics patients’ data encrypted due to ransomware attack
https://finance.yahoo.com/news/childrens-choice-pediatrics-notifies-patients-232600915.html
Exploit: Ransomware
Children’s Choice Pediatrics: Pediatric healthcare provider
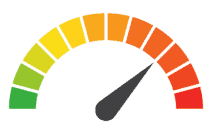
Risk to Small Business: 1.555 = Severe: A ransomware attack encrypted patient data and exposed patient records to hackers. The attack, which was discovered on October 27, 2019, encrypted the healthcare provider’s entire network. When records were restored, the provider discovered that some were irretrievably deleted. In response, Children’s Choice Pediatrics is upgrading its cybersecurity protocols to ensure that they don’t give a foothold to future ransomware attacks. However, the opportunity cost, reputational damage, and recovery expenses will continue to weigh down the practice now and for the foreseeable future.

Individual Risk: 2.285 = Severe: While hackers often encrypt company data to extract a ransom, many are turning to data theft as a means to exact additional money from a ransomware attack. In this case, some patients’ personally identifiable information may have been exposed to hackers. Those impacted by the breach should stay vigilant in monitoring their online accounts and scrutinizing digital communications as this data is often redeployed in phishing attacks that compromise additional data.
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Reactive cybersecurity measures can’t undo the damage of a data breach. With the holistic cost associated with exposure at an all-time high, companies have millions of reasons to embrace a robust defensive posture against cybercrime. Often, this means starting by securing accounts using best practices, like two-factor authentication, to keep intruders out.
Risk Levels:
1 - 1.5 = Extreme Risk
1.51 - 2.49 = Severe Risk
2.5 - 3 = Moderate Risk
*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.

