Hanna Andersson’s online store infected with payment skimming malware, stealing customer identifiable information
Exploit: Malware attack
Manor Independent School District: Children’s clothing maker
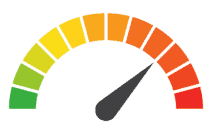
Risk to Small Business: 2.222 = Severe: Cybercriminals infected Hanna Andersson’s online store with payment skimming malware that collects customers’ personally identifiable information. The breach impacted customers shopping between September 16 and November 11, 2019. The company only identified the breach after being notified by law enforcement, and the consequences were exacerbated because Hanna Andersson failed to follow PCI standards for payment card encryption and CVV management. As a result, the company will likely face both customer blowback and regulatory scrutiny, neither of which will help the business thrive.

Individual Risk: 2.285 = Severe: Hackers obtained customers’ personal and financial data entered at checkout. This includes their names, shipping addresses, billing addresses, payment card numbers, CVV codes, and expiration dates. Unfortunately, it appears that some customers were already victimized by hackers, as law enforcement identified the breach because of fraudulent purchases made online using these credentials. Therefore, anyone impacted by the breach should immediately notify their financial institutions of the event. They also need to carefully review their account details for unusual or fraudulent activity. Credit and identity monitoring services can keep an eye on long-term misuse, ensuring that victims’ information remains secure even after the urgency of the matter has decreased.
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Payment skimming malware is a significant, ongoing threat for online retailers. It undermines customer confidence in the buying process and invites costly repercussions from a data breach. However, malware always requires a foothold to gain access to these systems, and every business can fight back by ensuring that their defensive posture is prepared for this increasingly common attack methodology.
Risk Levels:
1 - 1.5 = Extreme Risk
1.51 - 2.49 = Severe Risk
2.5 - 3 = Moderate Risk
*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.
