Slickwraps lack of basic protection exposes 850,000 customers’ personal data
Exploit: Unprotected database.
Slickwraps: Producer and distributor of hardware skins.
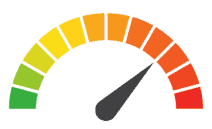
Risk to Small Business: 2 = Severe: The company’s databases lacked basic protections that exposed customer data to the internet. Slickwraps cited the long-term trust of its customers as a vital component of its business model, making this episode an especially problematic event for the business. The problem is compounded by the fact that an internet user tried to alert the company about the breach multiple times. Ultimately, Flickwraps discovered the breach after it was posted on Twitter.

Individual Risk: 2.428 = Severe: The company’s unsecured database exposed customer details to the internet. This included names, email addresses, physical addresses, phone numbers, and purchase histories. The breach does not extend to customers who accessed the online store as a guest, and it did not include financial data. Those impacted by the breach should be aware that this information can be used in spear phishing attacks or for other malicious purposes. They should be especially vigilant in monitoring online communications.
Customers Impacted: 850,000
How it Could Affect Your Customers’ Business: Slickwraps has been extremely apologetic after the breach. However, this contrite posture is no replacement for simple steps that they could have taken to secure company and customer data from day one. Customers and regulatory authorities expect companies to follow basic best practices when dealing with sensitive data, and the company’s apologetic tone is unlikely to help avoid a negative fallout from the incident.
Risk Levels:
1 - 1.5 = Extreme Risk
1.51 - 2.49 = Severe Risk
2.5 - 3 = Moderate Risk
*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.

